Worried about Ransomware? If you’re on Mac OS X you’re safe – for now
Some good news has been released today for Mac OS X users who are worried about their PCs getting infected with ransomware: a security researcher has just developed a free security tool to keep your desktop safe.
Ransomware, which is a type of malware which infects your computer and essentially blocks certain functions or processes from occurring, rendering your PC essentially useless until you send a fee, or a “ransom” to the hackers who have infected your system.
The security tool, called RansomWhere? was created by Patrick Wardle, the Director of Research and Development at Synack, a security firm. The tool works to detect attempts at encryption from outside and unknown processes by monitoring users’ home directories and monitoring when encrypted files are created rapidly inside of them, which is one of the giveaways that indicates ransomware activity.
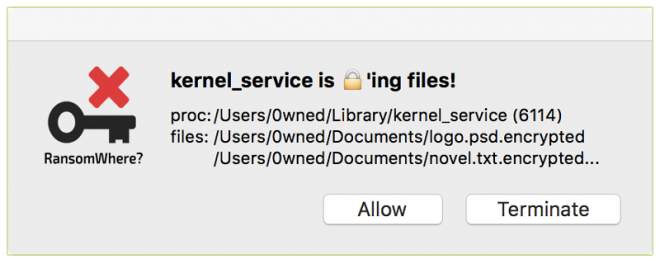
When RansomWhere? detects this kind of activity is detects the processes responsible for the file creation and suspends its ability to continue, and notifies the user of it’s findings. Then, it prompts the user to either continue with the file installation, or to terminate it.
In order to successfully detect instances of Ransomware, RansomWhere? whitelists all applications signed by Apple, and the majority of any apps which may have already been installed on the user’s Mac when it is first installed. This means that RansomWhere? needs to be installed on a Mac which has not previously been infected by Ransomware.
“RansomWhere? was designed to generically stop OS X ransomware,” Wardle said in a blog post on his website Objective-See. “However several design choices were consciously made — to facilitate reliability, simplicity, and speed — that may impact its protection capabilities. First, it is important to understand that the protections afforded by any security tool, if specifically targeted, can be bypassed. That is to say, if a new piece of OS X ransomware was designed to specifically bypass RansomWhere? it would likely succeed.”
“From a user’s point of view, it really sucks,” Wardle said in an interview with Business Insider on Wednesday. “Even if they’re [following] best security practices — they haven’t turned off Gatekeeper [Apple’s anti-virus software], they’re not downloading shady apps from random sites — they still would have gotten infected.”
This is good news for Mac OS X users, who may have been feeling some stress as ransomware hackers have begun to move from targeting only Windows PCs, to a broader range of operating systems. Currently there are already versions of ransomware which can infect Linux-based systems, so it’s only a matter of time before hackers begin spreading to Mac OS X systems, as well.
As always, here at Corey’s Computing we’ll be publishing updates about viruses, ransomware, and other threats to your computer’s performance and security here on our blog, so make sure to check back soon.
Petya, the latest in “crypto-extortion” malware

PC users, beware! There’s a new form of malware making the rounds online, and it’s taking crypto-extortion to a whole new level, according to Ars Technica.
The malware is called Petya, and unlike most forms of malware, which are programmed to be distributed to a wider and more general user base, this ransomware is targeted specifically at individuals who work in departments like human resources (HR) and information technologies (IT).
What is Ransomware?
Cryptographic ransomware, or just “ransomware” is a type of malware which restricts access to the infected PC in a specific way until the victims pay a ransom to the malware operators in exchange for removing the restriction.
What Makes Petya Different?
Unlike most forms of ransomware, which are selective about what they encrypt so the victims have enough access to their PCs to pay the hackers, Petya targets your entire startup drive, encrypting the master file table so that Windows can’t make sense of the index files on your disk. This process essentially leaves all of your programs and files intact, but scrambles the metadata so that Windows can’t turn the data into anything useful.

How Are People Getting It?
Petya is currently being delivered via Dropbox links in e-mails being sent to human resources companies. The links claim to be connected to important applications to be installed by the employee, but when they run the attachment a Window alert pops up warning them that it might be trouble.
In the unfortunate circumstances where an employee clicks ‘continue’ Petya is launched and inserted into the master boot record (MBR) and the system restarts. When the victim reboots the computer, the randomware performs a fake disc check (CHKDSK) and warns “One of your disks contains errors and needs to be repaired” after which an ASCII skull and crossbones appears and the message “You became victim of the PETYA RANSOMWARE!” is displayed.
The screen then shows instructions on how to obtain a key to restore the disc after the victim pays a ransom, usually around 0.90294 Bitcoins, or $373 at current Bitcoin value.
Some Good News, and Bad News
The good news is that as if you’re a regular PC user like many of our customers, you should be just fine and you’ll never have to worry about Petya infecting your system.
The bad news is that if you find your PC infected with this aggressive form of malware, you may find yourself unable to unscramble your metadata to make sense of the programs and files you used to have.
This means that the only way to recover some (potentially not all) of your files is to enlist the help of a dedicated data recovery service.
The Bottom Line?
As always, the easiest way to keep your PC safe from malware and viruses is to not open emails that look suspicious and don’t click on links or open folders from people you don’t know.
However, if your PC is acting up, running slowly, generating pop-ups at random, or displaying other warning signs of infection and malware, bring it in for our virus removal service and we’ll clean it up for you.

